Cloud computing has become an essential tool for businesses of all sizes, providing a flexible, cost-effective, and scalable solution for managing your data and applications. However, as an increasing number of companies move their operations to the cloud, the number of cloud computing security threats have increased significantly.
In this blog post, we’ll discuss the most common cloud computing security threats your business should look out for – as well as some steps you can take to keep your cloud secure.
Did you know that an alarming 45% of all data breaches occur within cloud environments?
Although still the more reliable option over traditional data centers, taking the necessary steps in maintaining your cloud security posture is essential to the long-term survival of your business. Especially considering that 60% of SMBs that fall victim to a cyber attack go out of business within six months.
Here are some of the most common cloud security threats in business:
Data Breaches: Data breaches are the most common cloud security threat faced by businesses. Data breaches occur when hackers gain unauthorized access to sensitive information stored in the cloud. This information can include customer data, financial information, and proprietary business information.
Account Hijacking: Account hijacking occurs when a hacker gains access to a user’s cloud account by stealing login credentials or exploiting a vulnerability in the system. Once the hacker gains access, they can steal or manipulate data, send spam emails, or launch attacks against other systems.
Get a Complimentary Vulnerability Assessment
Contact Us
Insider Threats: Insider threats occur when an employee or contractor with access to the cloud system intentionally or unintentionally causes a security breach. This can be due to negligence, malicious intent, or a lack of security training.
Malware Attacks: Malware attacks occur when a hacker injects malicious code into the cloud system, which can then spread to other systems. Malware can be used to steal data, launch attacks, or cause other types of damage to the system.
Distributed Denial of Service (DDoS): DDoS attacks occur when multiple compromised systems are used to flood a targeted system with traffic, overwhelming it and making it unavailable to users. This can result in significant downtime and loss of revenue for companies relying on the cloud.
These threats are successful because they target vulnerabilities in the cloud system, such as weak passwords, unsecured data, and outdated software.
So what can you do to secure your cloud platforms?
Recently, more and more businesses have made the decision to turn to a managed service provider (MSP) for assistance in implementing cloud security solutions to stay protected against these cloud security threats.
As a result, the cloud security market is expected to account for $75.77 billion by 2029.
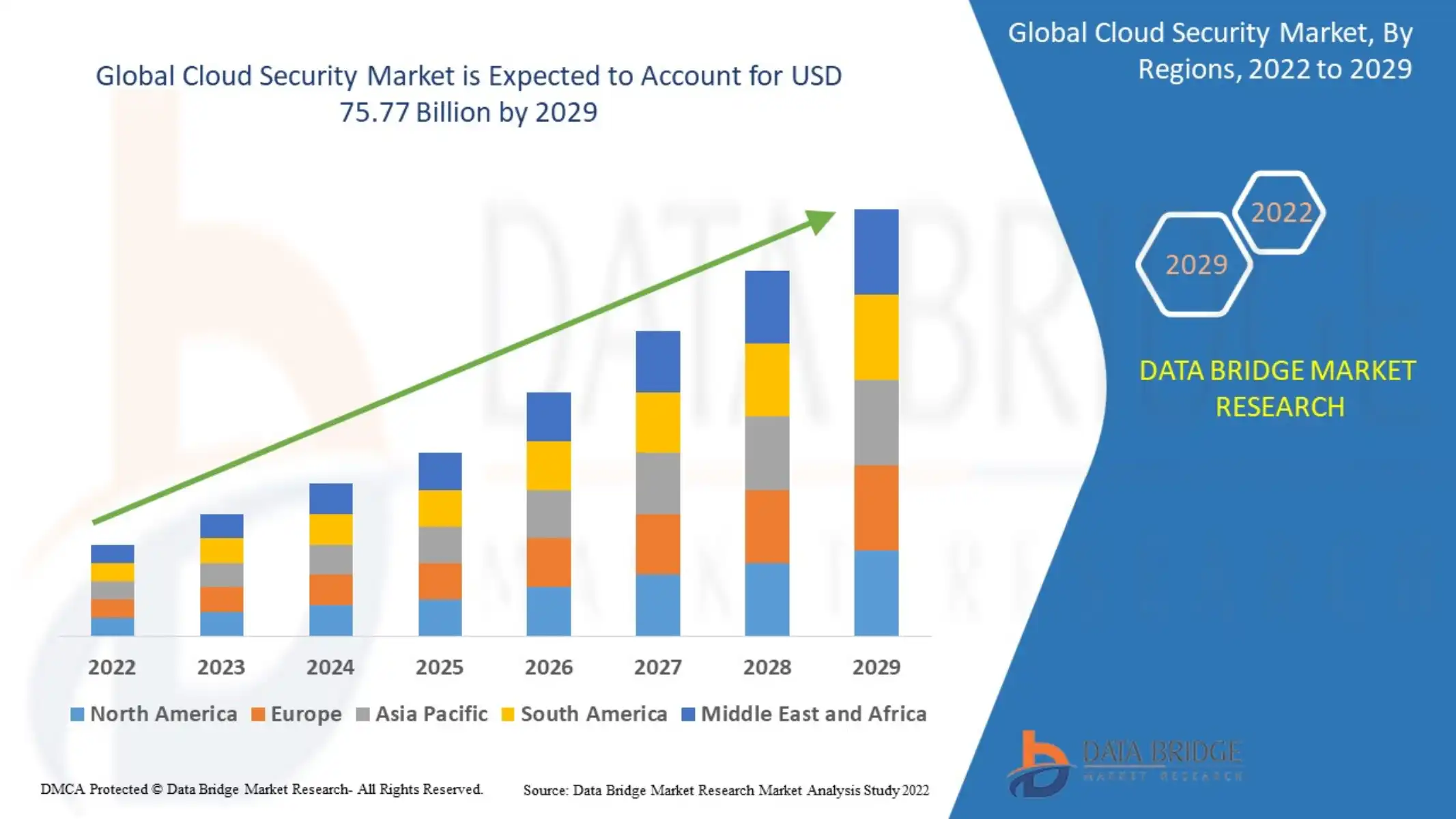
Image Credit: Data Bridge Market Research
Let’s take a look at some of the steps you can take to mitigate the risk of these cloud computing security threats.
Access management helps keep data protected by ensuring that only authorized users can access sensitive information, and that access is granted based on a user’s role, job function, and level of authority.
From implementing, configuring, to monitoring and maintaining your access controls, MSPs can assess your business’s security needs and determine the appropriate access management solution based on your specific requirements.
In the event that an attack surfaces, multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide two or more forms of identification to access the cloud system. This can include a password, a security token, or a biometric factor such as a fingerprint or facial recognition.
MSPs can help implement MFA by providing expertise, tools, and support to ensure that the MFA solution is configured correctly and works seamlessly with your existing cloud infrastructure.
| Check out these additional resources to learn more about why digital security is important and how to choose an MSP that can meet your cloud security needs: |
Encrypting data is an effective way to protect sensitive information and avoid security threats in cloud computing.
Encryption scrambles the data so that it can only be read by someone with the encryption key. This makes it difficult for hackers to access the data even if they gain unauthorized access to the system.
Keeping software up-to-date is a crucial component in any cloud security strategy, as software updates often contain security patches that address known vulnerabilities in the system.
Failure to update software can leave your system vulnerable to attack, so it’s best to schedule routine software updates in order to mitigate these security risks.
Regular security audits can help you identify potential vulnerabilities in your cloud system, prevent data loss, and further mitigate security threats in cloud computing.
This can include checking for weak passwords, outdated software, and unsecured data. By identifying these security challenges, you can take steps to address them before they are exploited by hackers.
Providing security training to your internal team members can help prevent insider threats significantly – considering that 88% of security breaches are a result of human error.
Cloud-based security training can include training on how to create strong passwords, how to recognize phishing emails, and how to avoid unintentional data breaches.

With 16+ years of industry experience, Complete Network can help keep your data safe by providing comprehensive cloud security solutions tailored exclusively to your needs.
To enhance your security posture and reduce the risk of unauthorized access to sensitive data and applications, get in touch with us today!
In an ideal world, technology would be a consistent source of competitive advantage and benefit for small and midsized businesses. The reality is that many fail to realize that confidence.
Without the right resources and support, even a highly skilled technology team can become overwhelmed by the growing list of technology management duties. When important tasks get neglected, it creates ripple effects throughout an organization that damage productivity and efficiency.
The co-managed IT services model solves these problems by providing your existing IT team with all the support and resources they need to successfully plan, manage, and defend your network technology.
This guide covers:
Download it for free by filling out the form here.
