Leveraging an outsourced IT company can help create the right IT policies to minimize uncertainty and risk while maximizing accountability and efficiency.
Policies help your employees make good decisions when using company technology. They also better define your culture, eliminate inconsistency, reduce human error, and ensure security and productivity. Working with an outsourced IT company can ensure your business will benefit from strategic IT policies.
Despite the many benefits of having a clearly defined set of IT policies, many growing businesses still haven’t spent the time and effort to develop them. Often, they lack the right skills. Meaningful IT policies must be customized to the needs and goals of your organization, and without the right in-house expertise, the task can quickly become overwhelming.
In this article, we’ll put our our expertise as an award-winning IT company to use to guide you through some of the best practices for building the three most important types of IT policies in 2020.
An acceptable use policy (AUP) – sometimes called an Internet usage or acceptable IT usage policy – is a document that explains how your staff can use your company’s technology. It outlines permissible behavior, helps to clarify forbidden activities, and ensures that company contracts and agreements are all honored.
Having an AUP helps your organization in several important ways.
Designing an AUP takes careful planning. You should start by considering the greater legal environment. What are the state and local data security laws, or compliance requirements, that should inform the content of your AUP? Are there cloud computing systems, social media tools, or marketing software that could cause legal problems for your business?
Once you’ve done a thorough analysis of your network, you can begin drafting an AUP. Some of the best practices for designing an AUP include:
Small and midsized businesses have faced an annual increase in the number and financial impact of cyberattack for several years in a row. While next-generation threats like AI-powered malware and advanced phishing techniques are partially to blame, employee error is still the most common cause of network infiltration, data loss, and downtime.
Developing a strong information security policy is one of the most effective tools to protect your business from attack. It can help to ensure that intrusion attempts are dealt with in an organized and effective way. An InfoSec policy can help your organization achieve the following:
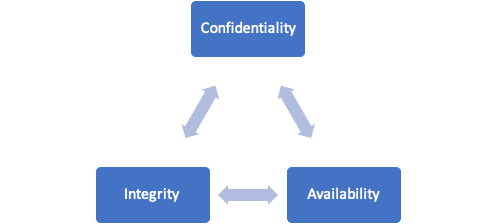
Within the general information security policy, you may also want to define policies for the security of specific systems, ensuring the CIA triad of confidentiality, integrity, and availability are maintained across your entire organization.
VPN Usage Policy
As more users access company resources from outside the office, establishing and enforcing a clear VPN policy can ensure that VPN access is only used for company affairs, that copyright infringement and other illegal activities are restricted during VPN usage, and that you properly establish personal responsibility for any illegal activity.
Password Policy
Strong passwords can be an effective first line of defense if they’re implemented uniformly across all systems. An effective password policy will ensure that staff members are creating strong passwords, not reusing them across different applications and devices or not updating them frequently enough, and more.
Remote Access Policy
In a time of increasing work-from-home jobs, it’s important that businesses have a clear set of rules to govern the access of company resources from remote locations. This should include the following elements:
Even more than the AUP, designing an InfoSec policy requires the expertise of a skilled IT team, like Complete Network. We’ll analyze your organization’s technology and processes, develop InfoSec policies that balance the needs of your security and business departments, then guide you through the implementation and enforcement of those policies, helping to ensure program success.
The need for strong policies around mobile devices is urgent. Shadow IT and IoT devices, unauthorized devices that are not managed by the IT department, are connecting to business networks in greater numbers every year. These devices are a major security liability for companies without strict rules for user behavior.
Mobile device policy is a balancing act. It should both be comprehensive enough to protect company assets and reasonable enough that you reap the cost savings and convenience of BYOD. Below are some of the current best practices for mobile policy making, which you can use to guide your own efforts:
Here’s a list of additional resources for creating an information security policy.
For over 20 years, Complete Network has been helping organizations in Albany, New York, Charlotte, North Carolina, and Bluffton, South Carolina to optimize the reliability and security of their technology with clearly defined processes, procedures, and policies. If your company needs help developing or enforcing IT management policies, our team of network engineers would be happy to help. A clearly defined policy can empower your IT support.
Contact the friendly Complete Network team any time with your questions at 1-(844) 426-7844.
In an ideal world, technology would be a consistent source of competitive advantage and benefit for small and midsized businesses. The reality is that many fail to realize that confidence.
Without the right resources and support, even a highly skilled technology team can become overwhelmed by the growing list of technology management duties. When important tasks get neglected, it creates ripple effects throughout an organization that damage productivity and efficiency.
The co-managed IT services model solves these problems by providing your existing IT team with all the support and resources they need to successfully plan, manage, and defend your network technology.
This guide covers:
Download it for free by filling out the form here.

This will close in 0 seconds
This will close in 0 seconds