Cyber threats such as cyber vandalism are the most consistent challenge confronting business leaders in the world today, an idea supported by countless industry statistics.
This recent report from insurance giant Allianz found that cyberattacks are the number one concern of business leaders, taking precedence over inflation, supply chain disruptions, and geopolitical instability. Other research from Accenture found that 81% of that same group believes staying ahead of cybersecurity risks is a constant battle.
“The sheer diversity in the types of cyber threats means there is no “one-size-fits-all” security solution, each type of attack—viruses, data breaches, DDoS attacks, and cyber vandalism—necessitates a separate and unique response,” says Jeremy Wanamaker, CEO of Complete Network.
But what is cyber vandalism? In this article, we’ll look at:
First things first: what is cyber vandalism? Cyber vandalism, by definition, (sometimes called electronic vandalism or computer vandalism) is any malicious activity carried out with the intent to deteriorate, disrupt, or deface computer systems, networks, or websites.
Data vandalism, by definition, similarly refers to the intentional and malicious act of altering, destroying, or defacing digital data with the intent to cause harm, disrupt operations, or compromise the integrity and usefulness of the information.
The motivation behind cyber vandalism and data vandalism varies widely from case to case, from attackers seeking personal gratification, a wish to showcase dissent or express ideological beliefs, to even just the desire to create havoc.
Except for a few notable exceptions, cyber vandalism rarely draws the same sensationalist mainstream headlines as other cyberattacks. This has caused some people to wrongly label these attacks as “petty” cybercrimes.
As you’ll soon see, not taking computer vandalism seriously is flawed.
Gone are the days when cybercrime can only be launched by skilled computer experts with deep networking or programming knowledge. Those weapons are now available “as a service” to criminals of any skill level to purchase.
Low-level “script kiddies” and amateur hackers are empowered to wreak devastation using off-the-shelf tools available on GitHub or dark net forums for just a few dollars. All that’s required to launch those attacks is a simple reconnaissance mission to map your network and cross-reference the systems against an open-source common vulnerabilities and exposures (CVE) database.
After they find a “hit,” commercially available malware kits do the heavy lifting of exploiting the vulnerability and extorting your business. If you pay the demand, the funds are split between the provider and the “affiliate” hacker who supplied the information on the target.
Sounds scary, right?
Not all cybercriminals are driven by financial gain. In some cases, attacks are intended to make a political statement or purely for the “lulz,” an online term for kicks or laughs.
The FBI received more than 800,000 complaints related to cyber attacks in 2022, with losses from cyber crime totaling over $10 billion.
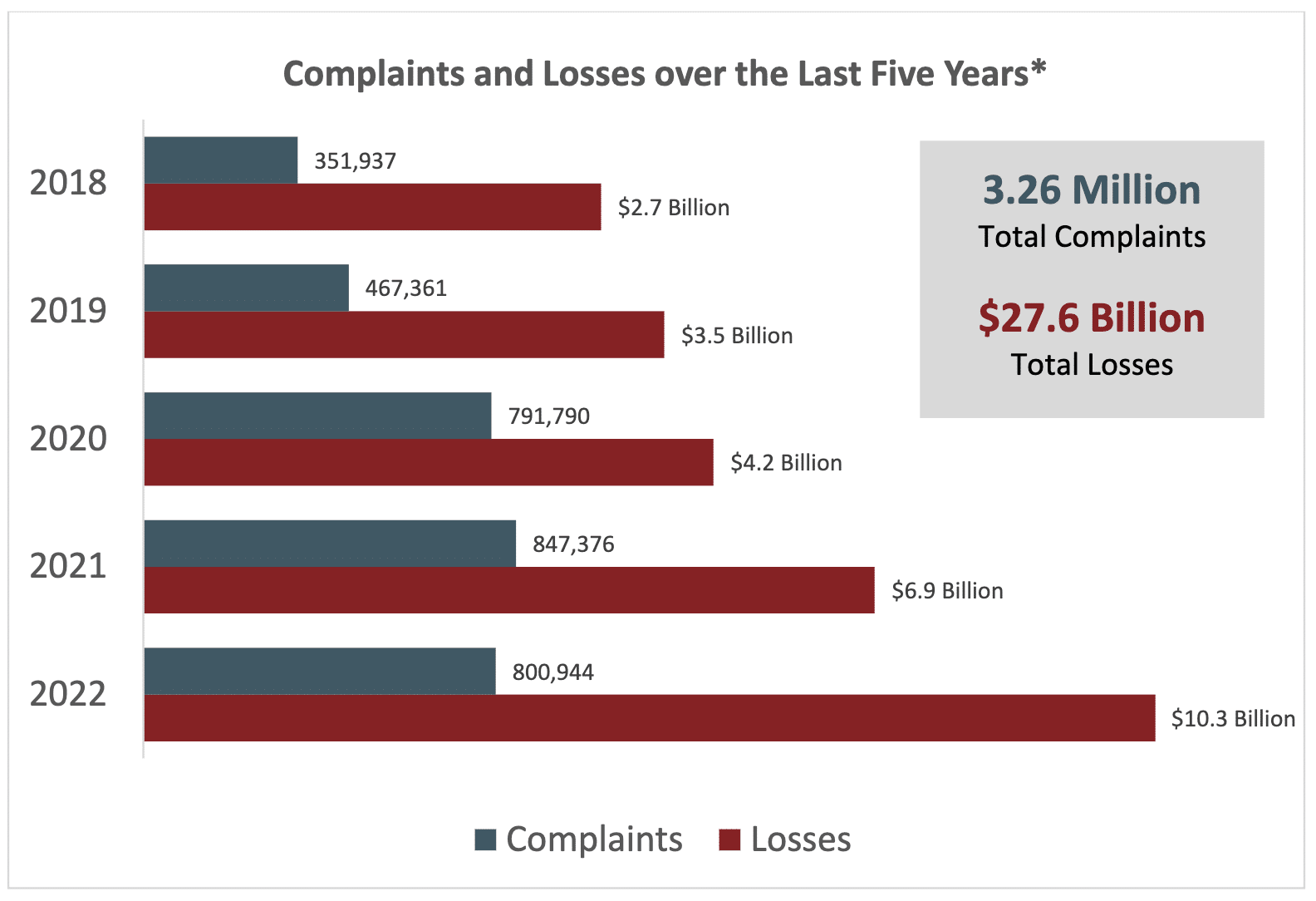
Image Credit: Security Week
While some perceive electronic vandalism attacks as minor crimes, in the following sections, we’ll shed light on the common types of vandalism, the profound implications they have on victims, and proven ways to fight back.
In January 2020, two Iranian script kiddies wanted to protest the American killing of the Iranian general Qassem Soleimani. The duo defaced dozens of websites owned by innocent American businesses, with pro-Iranian slogans and messages. However, they were able to secure the attention they desired by defacing the official website of the U.S. Federal Depository Library with graphic images of a battered and bruised President Trump.
Social media takeovers are another common form of cyber vandalism. Hackers typically use social engineering or cracked passwords to gain access to target accounts. Once logged on, they will usually either discredit the victim or leak sensitive information about the organization, as was the case when terrorist sympathizers hacked the Twitter account of US Military Central Command.
Denial of service attacks are one of the oldest forms of electronic vandalism in use. While companies have gotten much better at thwarting them, attackers are changing tactics, too. GitHub was targeted by one of the largest DDoS attacks on record in 2018. The attacker sent a whopping 126 million packets per second! But unlike most DDoS attacks that need massive swarms of botnets, this attacker used an attack that flooded GitHubs’ database caching system with phony requests.
In recent years, the number of such attacks has only increased. In 2022, DDoS attacks grew by 150% year-on-year, while also increasing in complexity.
Learn More About How We Can Help
Contact Us
What is cyber vandalism’s impact on your business? Cyber vandalism can inflict just as much devastation on victims as other cybercrimes. In this section, we’ll take a closer look at the hidden costs of cyber vandalism, including reputational harm, financial loss, and psychological trauma.
Reputational harm – Perception is reality. And to non-technical observers who don’t understand the inner workings of an attack, a hack is a hack. They don’t differentiate between data breaches and website defacements; they simply see that hackers won the battle by compromising your computer systems.
As a result, they lose faith in your company and opt for alternatives. Recovering from such an exodus can take several years and cost untold sums of money.
Financial loss – Costs associated with downtime, incident response and recovery, and higher insurance premiums can quickly accumulate following an act of cyber vandalism against your company.
Psychological trauma – Oftentimes the pain of cyber vandalism can’t be expressed in dollar terms. That was the case when hackers stole private user data from a dating site for married individuals seeking affairs called Ashley Madison.
After the data theft, hackers vandalized the homepage with an ominous threat to release names, addresses, and private messages with users’ explicit photos.
Despite the debate surrounding the controversial nature of the site, it’s easy to empathize with the sense of panic and psychological trauma users faced during this ordeal. Check out these additional resources to learn more:
| Resources: |
Cyber vandals use many of the same targeting and exploitation techniques as other cybercriminals. As such, the ways to prevent computer vandalism are virtually identical to the ways to prevent other types of malicious attacks.
Strong Password Policies
Compromising credentials ranks among the most favored tactics employed by hackers to breach victims’ systems. Thus, the significance of enforcing strong password policies cannot be overstated. It is considered best practice for your organization to establish clear guidelines that define, regulate, and oversee the management of all employee keys, passwords, and accounts.
Cybersecurity Awareness Training
Routine cyber awareness training done at least semi-annually fosters a cybersecurity culture in your organization. It enhances workforce threat knowledge, which greatly reduces cyber risks, modifies behavior, and better shields the business against hostile actors.
Patch Hardware and Software
Using unpatched or outdated infrastructure exposes organizations to severe cybersecurity threats. Publicly available CVE databases list common vulnerabilities in popular equipment from the likes of Arista, Juniper, Cisco, Microsoft, Palo Alto Networks, Dell, and HP, among others. The best way to avoid these “low-hanging fruit” attacks is to actively maintain a regular patching regimen for all software and devices in use.
Partner with Security Providers
To stay ahead in outwitting your adversaries, you need to be honest in assessing your strong suits and your weaknesses. For many organizations, IT security is not an area of expertise. Rather than doing nothing about it, organizations should take proactive steps to improve their cybersecurity posture by working with a trusted security services provider. If your IT team needs assistance in its cybersecurity duties, we can help today.
Ensure Your Protection with Complete Network
| IT Support |
Complete Network has been a trusted outsourced cybersecurity provider for over two decades, earning consistent praise and 5-star reviews for our speed, friendliness, and reliability. Looking for a partner that you can trust? Contact our team at 844 426 7844 any time. We’re here to help!
In an ideal world, technology would be a consistent source of competitive advantage and benefit for small and midsized businesses. The reality is that many fail to realize that confidence.
Without the right resources and support, even a highly skilled technology team can become overwhelmed by the growing list of technology management duties. When important tasks get neglected, it creates ripple effects throughout an organization that damage productivity and efficiency.
The co-managed IT services model solves these problems by providing your existing IT team with all the support and resources they need to successfully plan, manage, and defend your network technology.
This guide covers:
This will close in 0 seconds
This will close in 0 seconds