Risk assessment frameworks are vital tools in risk management. They serve as structured guides to identify, evaluate, and mitigate risks in various contexts.
As organizations face an ever-evolving landscape of threats, the importance of implementing a robust risk assessment framework cannot be overstated.
| Jeremy Wanamaker, CEO of Complete Network, says, “It is a critical component that supports the decision-making process, enhances organizational resilience, and safeguards assets against potential threats.” |
In this article, we’ll explore risk assessment frameworks. We aim to provide foundational knowledge about risk assessment frameworks, their benefits and components, and their importance in hardening security posture.
By the end, the reader will have a firm grasp of the topic and be able to make informed decisions regarding their organization’s risk management practices.
A risk assessment framework or RAF provides a systematic approach for organizations to identify, evaluate, and articulate risks that could impact their business.
The overarching goal of an RAF is to organize and consolidate risk-related information so that the entire workforce is better aware of these challenges and can work in accord to address them.
Transform your approach with Complete Network's tailored risk treatment strategies.
Learn More
RAFs offer several benefits:
Source: TechTarget
In this section, we’ll delve into the four main types of risk assessment frameworks.
Each type offers a unique approach to discovering, evaluating, and mitigating risks within an organization. Knowledge of these core frameworks is crucial for developing effective risk strategies that align with your business goals and objectives.
Quantitative risk frameworks methodically measure and assign numerical values for how your risks are most likely to impact the business.
Usually, this is based on the probability and impact these risks will have on the overall cost, schedule, and quality of your outcomes.
Often, numbers alone don’t provide complete insight into your organization’s full risk spectrum. This is where qualitative risk assessments play a role.
Rather than numbers, qualitative frameworks rely heavily on first-hand observations, benchmarking, focus groups, reviews, and interviews. These techniques and tools can help organizations capture nuances and contexts that quantitative measures may miss.
Asset-based risk assessment frameworks evaluate risks by focusing on the assets that could be impacted.
They involve identifying and assessing the value, importance, and vulnerabilities of assets within an organization, such as physical assets like buildings and equipment, information assets like data and IP, and human assets like employees and intellectual capital.
Threat / Vulnerability-based frameworks are useful in managing weaknesses or gaps in an organization’s systems, processes, or controls that could be exploited by bad actors.
Understanding these vulnerabilities supports organizations in assessing the likelihood and potential impact of hacks and cyberattacks, as well as the core measures required to reduce or mitigate the vulnerabilities.
Let’s delve deeper into the various components that make up real-world RAFs. Here, we’ll explore the essential building blocks and provide a comprehensive understanding of how these components work together to form a complete framework.
Risk identification is the critical first step in the risk assessment.
Focused on identifying potential risks that could impact your business objectives, projects, or operations, this process involves an organized approach to identifying and documenting potential challenges that could lead to adverse consequences.
Internal factors that may be considered include the organization’s structure, culture, processes, and resources. For example, an organization with an outdated technology infrastructure may be more vulnerable to cyber threats.
External factors, on the other hand, include economic conditions, regulatory changes, market trends, and competitive pressures. For instance, a new competitor entering the market could risk an organization’s market share.
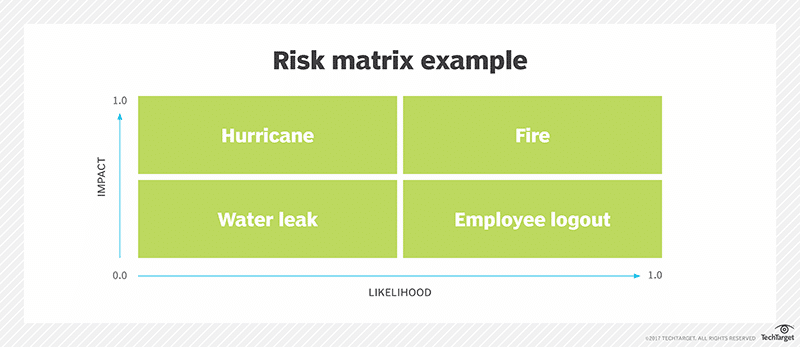
Once the organization has identified its risks, the next task is to evaluate and grade them based on their potential likelihood and impact.
The potential impact of a risk is calculated by considering the extent of harm it could cause to your underlying objectives, projects, or operations. Likewise, the likelihood of a risk occurring is assessed to determine the probability of it happening.
In addition to impact and likelihood, risk evaluation also considers the organization’s risk appetite and tolerance levels.
| More resources you might like: |
Risk treatment is the phase of the process where solutions are developed and implemented to address the identified risks. These solutions are based on the findings from your risk identification and evaluation.
One approach to risk treatment is risk mitigation, where actions are taken to reduce the probability that a risk will cause damage.
For example, implementing new processes or controls, investing in technology or infrastructure upgrades, or providing training to employees would serve as viable solutions.
Another approach is risk transfer, where the organization transfers the risk to another party, such as an insurance company. This is often done for risks that are beyond the organization’s control or for which the cost of mitigation is prohibitive.
In some cases, certain risks may be accepted by choosing not to take any action because the risk is deemed low or because the cost of mitigation outweighs the potential impact of the risk.
Maintaining detailed documentation serves several important purposes.
Firstly, it provides a clear and transparent record of the risk assessment process, including the rationale behind decisions made and the factors considered in prioritizing risks.
Secondly, documentation serves as a reference for future risk assessments. By documenting the outcomes of the current assessment, organizations can compare them with future assessments to identify any changes or trends in their risk profile.
Lastly, documentation helps track the effectiveness of risk mitigation measures.
Continuous RAF improvement is essential for ensuring the organization remains resilient and prepared to manage its risks for the foreseeable future.
Incorporating feedback, learning from past experiences, and adapting to changes in the risk landscape are the primary means for organizations to strengthen their risk management framework and protect their assets and operations.
Source: TechTarget
Now that we’ve explained what an RAF is, as well as the various benefits, types, and components therein, let’s take a look at the steps for choosing the right framework for your organization.
Thankfully, several proven and respected risk assessment frameworks are already available. Your organizational maturity, industry, and risk type will influence your choice.
Here are some of the leading frameworks:
| Consideration | Description | Importance |
| Organizational Context | Understanding the specific context within which the organization operates, including industry-specific risks and regulatory requirements. | Critical |
| Stakeholder Engagement | Involving stakeholders across various departments to ensure comprehensive risk identification and buy-in for the risk management process. | High |
| Integration with Existing Processes | Ensuring the risk assessment framework aligns with and enhances existing business and risk management processes. | High |
| Scalability and Flexibility | The framework should be adaptable to changes in the organization’s size, market, or risk environment. | Moderate to High |
| Continuous Monitoring and Review | Establishing mechanisms for ongoing monitoring and periodic review of the risk assessment framework to ensure its effectiveness and relevance. | Essential |
If your leadership team is looking to attain the highest level of confidence in selecting or creating a risk assessment framework, let us help.
The Complete Network team helps businesses in Albany, New York, Charlotte, North Carolina, Savannah, Georgia, and Bluffton, South Carolina help reduce risk and strengthen cybersecurity, while keeping cost and complexity under control.
Contact our friendly team at (844) 426-7844 and. We look forward to speaking with you!
In an ideal world, technology would be a consistent source of competitive advantage and benefit for small and midsized businesses. The reality is that many fail to realize that confidence.
Without the right resources and support, even a highly skilled technology team can become overwhelmed by the growing list of technology management duties. When important tasks get neglected, it creates ripple effects throughout an organization that damage productivity and efficiency.
The co-managed IT services model solves these problems by providing your existing IT team with all the support and resources they need to successfully plan, manage, and defend your network technology.
This guide covers:
This will close in 0 seconds
This will close in 0 seconds